
5.7.2025
Shankar Somasundaram founded Asimily in 2017 after years in senior roles at Symantec, where he developed a deep understanding of the growing security challenges posed by connected devices. At the time, most enterprise IoT environments were fragmented, poorly secured, and largely ignored by major cybersecurity vendors. Somasundaram recognized a dangerous gap in the market—one where attackers had far more agility than defenders.
Rather than start with an easier target, he chose one of the most complex and mission-critical environments: securing medical devices in hospitals, where the stakes were literally life or death. That focus forced Asimily to build a solution that was intelligent, non-disruptive, and deeply adaptable. The result is a platform capable of identifying and mitigating risks across vast networks of smart devices—many of which can’t easily be patched or replaced.
Today, Asimily protects not only healthcare systems but also organizations in hospitality and other industries where IoT usage is rising and the threat landscape is rapidly expanding. In this Spotlight Interview, Somasundaram discusses how hotel operators can better understand their evolving cyber risk profiles, how Asimily helps lean IT teams secure guest-facing infrastructure, and what risks may still be flying under the radar.
How does the cyber risk profile of hotels differ from other sectors like healthcare or retail, where Asimily also operates?
One of the key aspects that makes the hospitality sector unique is that there is much less control over physical access. It’s often said that when you lose physical access to a device, you’ve lost the cybersecurity battle. So, the very nature of the hospitality industry—where there are new people in proximity to your devices on a regular basis—puts hospitality cybersecurity defenders at a disadvantage from the get-go.
IoT has become central to modern guest experiences (smart thermostats, automated lighting, digital keycards, etc.). Adoption has accelerated, but how well do you think the hotel industry understands the cybersecurity implications of these technologies?
 Hotel industry headlines have, unfortunately, included several high-profile cybersecurity incidents concerning connected devices in recent years. Door locks are always a high-profile—and high-quantity—target. A hotel in Austria was hacked numerous times in a door-lock ransomware attack, for example.
Hotel industry headlines have, unfortunately, included several high-profile cybersecurity incidents concerning connected devices in recent years. Door locks are always a high-profile—and high-quantity—target. A hotel in Austria was hacked numerous times in a door-lock ransomware attack, for example.
But more and more devices are being added, which can create pivot points or denial of service opportunities. Occupancy sensors, which help ensure that room cleaning is done by someone who is actually in or near the room, are just one small example of the hidden ways in which the hospitality industry is dependent on the Internet of Things for the highest quality possible guest experiences.
Major hospitality brands were hit with cyberattacks in just the past year. What do these incidents tell us about common security gaps in hospitality environments?
Hospitality is just as vulnerable as industries that get more attention, such as healthcare and manufacturing. Where there is an opportunity to harm an experience or a brand or to steal information, criminals will find their way.
A lot of hotels rely on devices—HVAC controllers, smart TVs, POS terminals—that weren’t built with security in mind. How does Asimily’s platform tackle the challenge of securing these hard-to-update, mission-critical endpoints?
Asimily has a number of capabilities to protect devices in the environment.
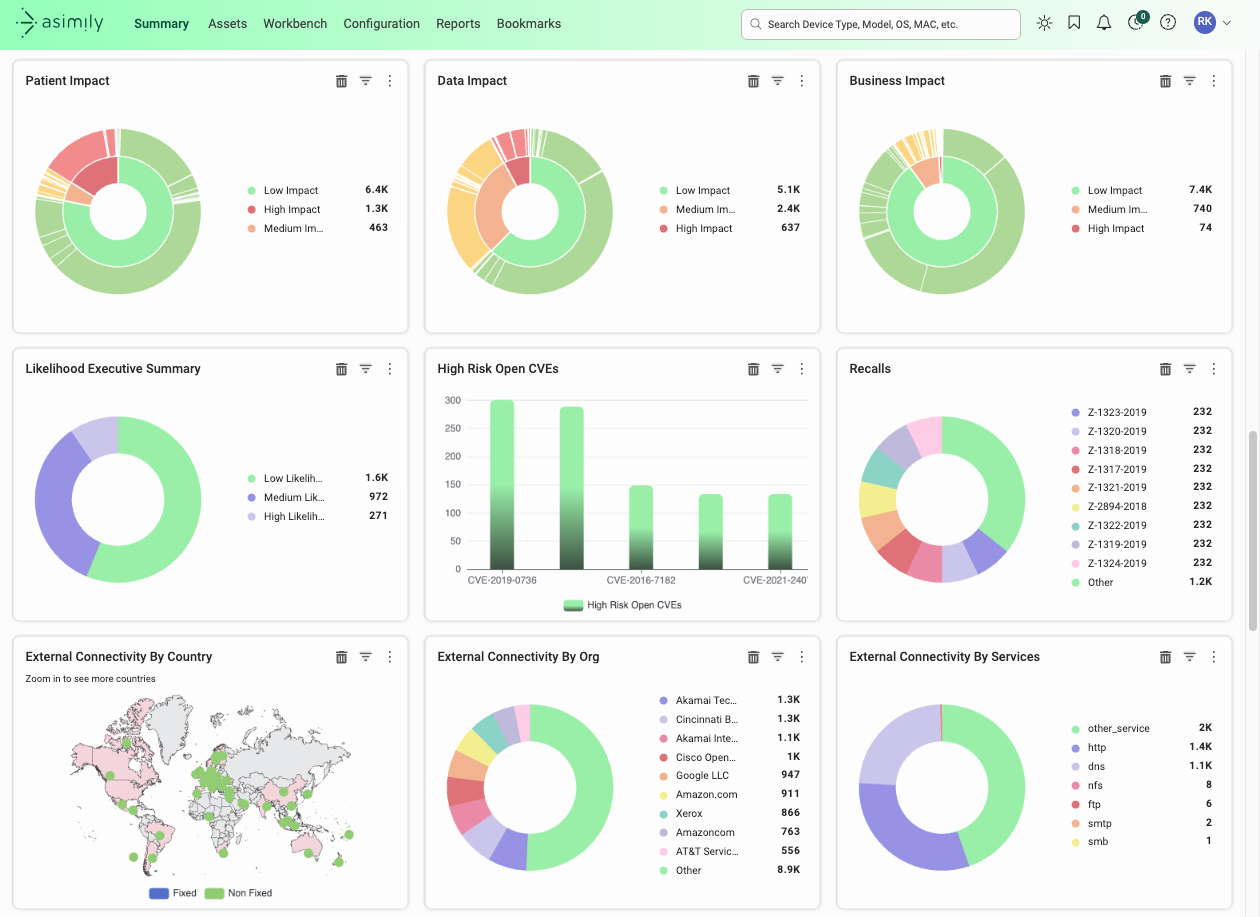 Our solution identifies devices and prioritizes the vulnerabilities that are most critical. To mitigate the risks in an environment, Asimily takes a multi-pronged approach. To begin with, Asimily can directly patch these IoT devices. Such a patch can be done on demand or within certain time parameters to ensure it is not disruptive.
Our solution identifies devices and prioritizes the vulnerabilities that are most critical. To mitigate the risks in an environment, Asimily takes a multi-pronged approach. To begin with, Asimily can directly patch these IoT devices. Such a patch can be done on demand or within certain time parameters to ensure it is not disruptive.
The result of industrial-strength patching is that the exposure window for unpatched devices is shorter, making it just that much harder for attackers to succeed and that much easier for them to move on. In cases where it is not possible to patch a device, Asimily uses a patented Attack Vector Analysis algorithm to understand the different ways attackers could exploit the device and block those attack vectors. Finally, Asimily can segment or microsegment such devices on the network where needed, allowing organizations to group and segment devices in any manner for the highest protection possible.
Can you walk us through a specific use case where Asimily helped a hotel group identify and mitigate a serious threat before it caused operational disruption?
An example that hit all of our customers across all industries was the Log4Shell vulnerability found in log4j. One of our customers required their teams to investigate each device to see if it ran the Java application and what application flags were set to see if the device was vulnerable to the exploit. This intensive effort would allow them to assess what devices were capable of being exploited so that their teams could then change the Java settings to protect that individual device.
Asimily was able to develop a simple policy rule that detected activity that Log4Shell-exploited devices would typically attempt. This helped customers get to a shortlist quickly, for further security protections. All of this was done before any patch was available and the customer was on their own.
How does prioritizing IoT risk vulnerabilities work for hotel operators who might be juggling limited security resources?
Asimily’s goal is to help even the smallest and most resource-strapped cybersecurity teams have the ability to defend their connected devices just as well as larger organizations. By putting capabilities that used to involve consultants into software, we are accelerating the ongoing evolution of device defense to try and keep ahead of the same efficiency gains made by attackers.
By prioritizing the top 2% of devices and providing efficient mitigations (patching, targeted attack prevention, segmentation), Asimily can help hotel operators mitigate risks with limited security resources.
Hotel IT teams are often small and stretched thin. What makes Asimily particularly well-suited to support lean teams who need to respond quickly to vulnerabilities without pulling systems offline?
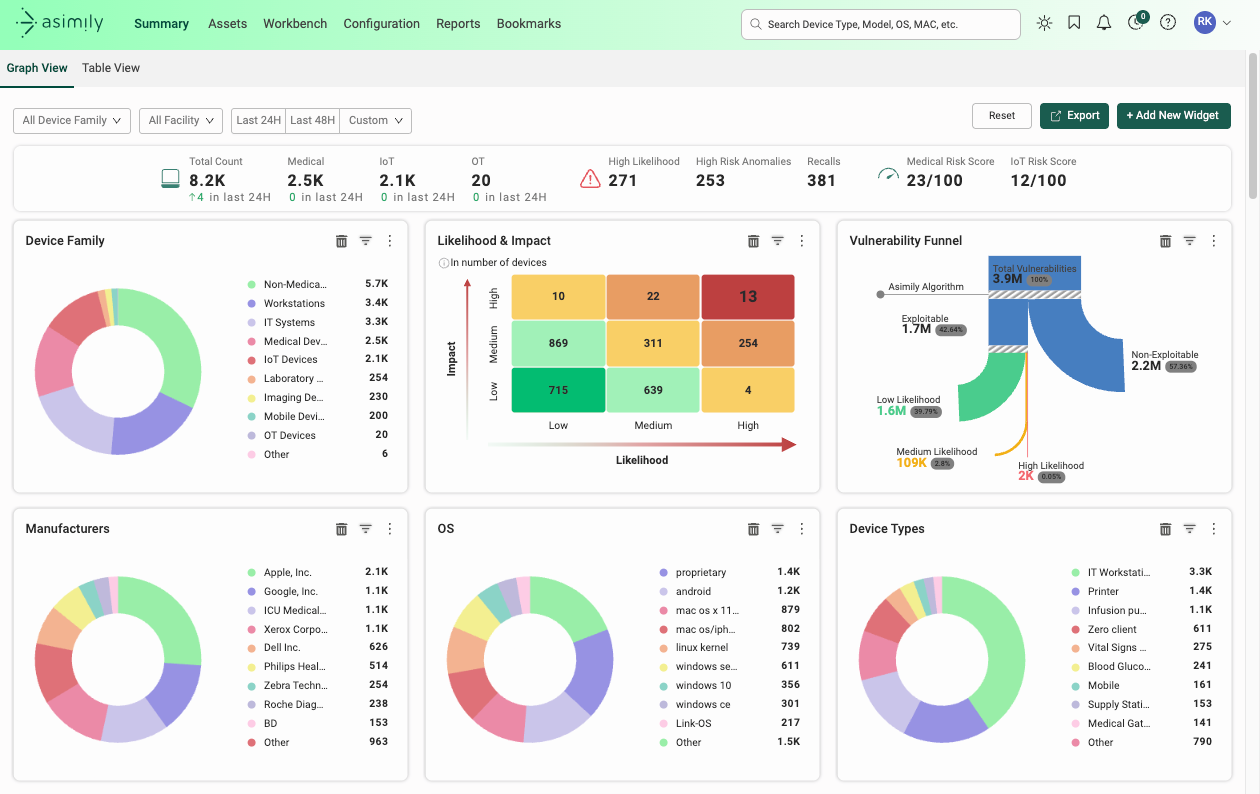 Many cybersecurity solutions are taking shortcuts when giving recommendations, and they don’t analyze the effort needed for mounting a defense against each new vulnerability. We do.
Many cybersecurity solutions are taking shortcuts when giving recommendations, and they don’t analyze the effort needed for mounting a defense against each new vulnerability. We do.
Often, simple suggestions involve making huge changes to infrastructure such as networking that, while eventually effective, need additional resources and time. They don’t always reduce risk now. Asimily focuses on the concept of Targeted Attack Prevention.
Targeted Attack Prevention is figuring out the simplest way to nullify an exploit chain, with the least effort. It must not impede the function of a device, but it should be catnip for time-strapped cybersecurity teams.
With growing adoption of self-service kiosks, digital check-in, and AI-powered concierge tools, what risks should hoteliers be thinking about that may not yet be on their radar?
While there are new risks that emerge as a result of new technologies, such as generative AI, I would recommend that hoteliers focus on the basics. Anything connected to the internet needs to be monitored, secured, and constantly hardened. Even the most innocuous device can be used as a pivot point to more valuable parts of a network.
In the hospitality business, guest experience is king. But security measures sometimes create friction. How does Asimily help strike that balance—protecting infrastructure without degrading the guest experience?
Asimily understands that cybersecurity should not impede experience. You could completely secure the network by quarantining every device, but then many of the devices would not work as expected, impeding guest experience.
This is why Asimily has developed different monitoring and mitigation capabilities that work in the background, seamlessly monitoring the environment and protecting against threats without impeding the customer experience.
What’s one overlooked risk factor that you believe most hoteliers should be paying closer attention to, and how should they begin to address it?
One key factor that is sometimes overlooked in complex hotel layouts is physical access. With guests having access to the amenities in the hotel, it’s easier to get in through the key systems.
It’s why we developed a module called Configuration Control as part of our solution’s advanced monitoring capabilities. This allows Asimily to snapshot every device, and if a device deviates from the snapshot due to some guest accessing and modifying the device, then the solution can detect and alert against the deviation.
By using advanced monitoring tools like Asimily, hoteliers can address overlooked risks and ensure these potential vulnerabilities don’t escalate into critical threats within their environment.
